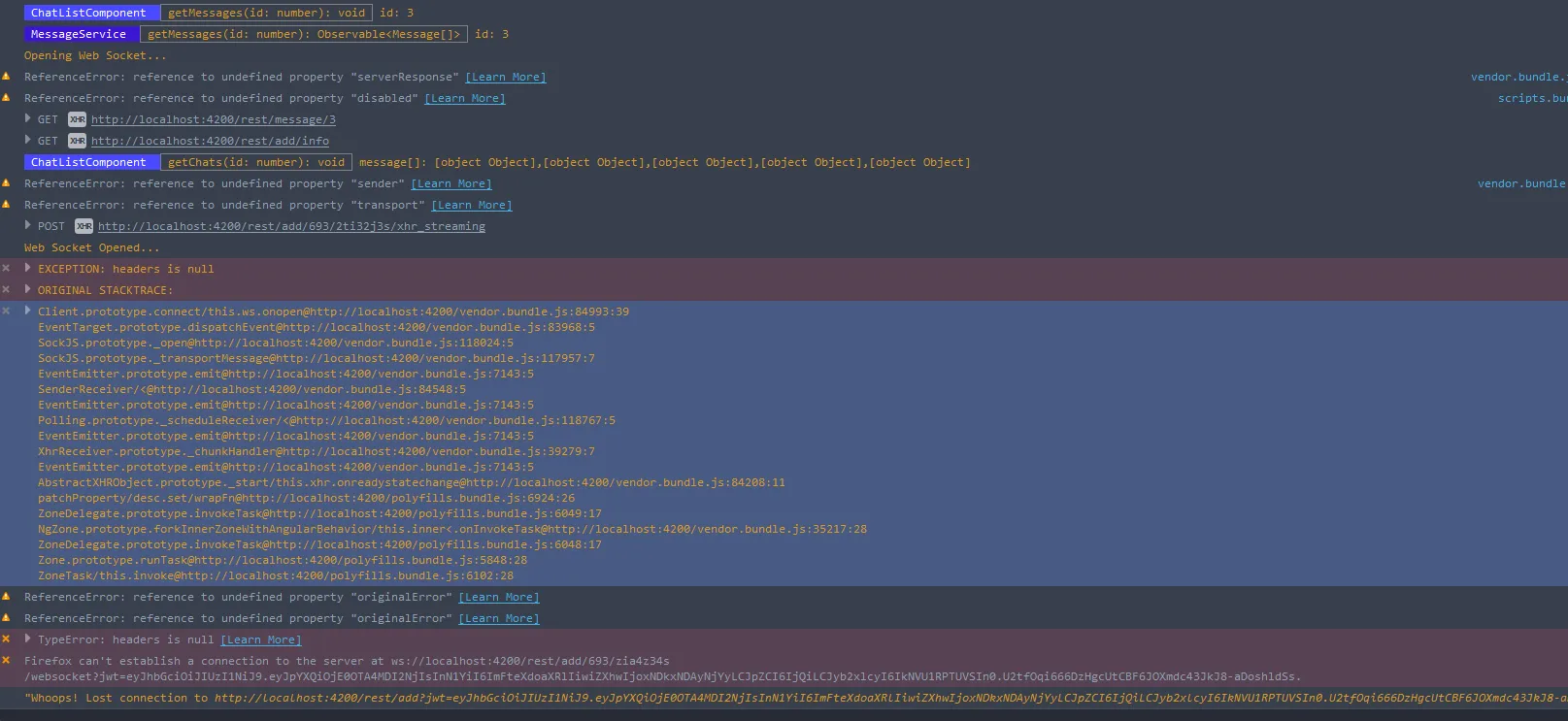
 angular2 connect()/subscribe()/send() - 都需要JWT令牌。
angular2 connect()/subscribe()/send() - 都需要JWT令牌。
public connect() : void {
let sockjs = new SockJS('/rest/add?jwt=' + this.authService.getToken());
let headers : any = this.authService.getAuthHeader();
this.stompClient = Stomp.over(sockjs);
this.stompClient.connect(this.token, (frame) => {
this.log.d("frame", "My Frame: " + frame);
this.log.d("connected()", "connected to /add");
this.stompClient.subscribe('/topic/addMessage', this.authService.getAuthHeader(), (stompResponse) => {
// this.stompSubject.next(JSON.parse(stompResponse.body));
this.log.d("result of WS call: ", JSON.parse(stompResponse.body).message);
}, (error) => {
this.log.d(error);
});
});
}
public send(payload: string) {
this.stompClient.send("/app/add", this.token, JSON.stringify({'message': payload}));
}JwtAuthenticationFilter.java
public class JwtAuthenticationFilter extends AbstractAuthenticationProcessingFilter {
public JwtAuthenticationFilter() {
super("/rest/**");
}
@Override
protected boolean requiresAuthentication(HttpServletRequest request, HttpServletResponse response) {
return true;
}
@Override
public Authentication attemptAuthentication(HttpServletRequest request, HttpServletResponse response) throws AuthenticationException {
String token = null;
String param = request.getParameter("jwt");
if(param == null) {
String header = request.getHeader("Authorization");
if (header == null || !header.startsWith("Bearer ")) {
throw new JwtAuthenticationException("No JWT token found in request headers");
}
token = header.substring(7);
} else {
token = param;
}
JwtAuthenticationToken authRequest = new JwtAuthenticationToken(token);
return getAuthenticationManager().authenticate(authRequest);
}
@Override
protected void successfulAuthentication(HttpServletRequest request, HttpServletResponse response, FilterChain chain, Authentication authResult) throws IOException, ServletException {
super.successfulAuthentication(request, response, chain, authResult);
// As this authentication is in HTTP header, after success we need to continue the request normally
// and return the response as if the resource was not secured at all
chain.doFilter(request, response);
}
}
JwtAuthenticationProvider.java
@Service
public class JwtAuthenticationProvider extends AbstractUserDetailsAuthenticationProvider {
@Autowired
private SecurityService securityService;
@Override
public boolean supports(Class<?> authentication) {
return (JwtAuthenticationToken.class.isAssignableFrom(authentication));
}
@Override
protected void additionalAuthenticationChecks(UserDetails userDetails, UsernamePasswordAuthenticationToken authentication) throws AuthenticationException {
}
@Override
@Transactional(readOnly=true)
protected UserDetails retrieveUser(String username, UsernamePasswordAuthenticationToken authentication) throws AuthenticationException {
JwtAuthenticationToken jwtAuthenticationToken = (JwtAuthenticationToken) authentication;
String token = jwtAuthenticationToken.getToken();
User user = securityService.parseToken(token);
if (user == null) {
throw new JwtAuthenticationException("JWT token is not valid");
}
return new AuthenticatedUser(user);
}
}
JwtAuthenticationSuccessHandler.java
@Service
public class JwtAuthenticationSuccessHandler implements AuthenticationSuccessHandler {
@Override
public void onAuthenticationSuccess(HttpServletRequest request, HttpServletResponse response, Authentication authentication) {
// We do not need to do anything extra on REST authentication success, because there is no page to redirect to
}
}
RestAuthenticationEntryPoint.java
@Service
public class RestAuthenticationEntryPoint implements AuthenticationEntryPoint {
@Override
public void commence(HttpServletRequest request, HttpServletResponse response, AuthenticationException authException) throws IOException {
// This is invoked when user tries to access a secured REST resource without supplying any credentials
// We should just send a 401 Unauthorized response because there is no 'login page' to redirect to
response.sendError(HttpServletResponse.SC_UNAUTHORIZED, "Unauthorized");
}
}
Websocket 配置:
<websocket:message-broker
application-destination-prefix="/app">
<websocket:stomp-endpoint path="/add">
<websocket:sockjs />
</websocket:stomp-endpoint>
<websocket:simple-broker prefix="/topic, /queue" />
</websocket:message-broker>
我的Spring Security
<context:component-scan base-package="com.myapp.ws.security"/>
<sec:global-method-security pre-post-annotations="enabled" />
<!-- everyone can try to login -->
<sec:http pattern="/rest/login/" security="none" />
<!--<sec:http pattern="/rest/add/**" security="none" />-->
<!-- only users with valid JWT can access protected resources -->
<sec:http pattern="/rest/**" entry-point-ref="restAuthenticationEntryPoint" create-session="stateless">
<!-- JWT is used to disabled-->
<sec:csrf disabled="true" />
<!-- don't redirect to UI login form -->
<sec:custom-filter before="FORM_LOGIN_FILTER" ref="jwtAuthenticationFilter" />
</sec:http>
<bean id="jwtAuthenticationFilter" class="com.myapp.ws.security.JwtAuthenticationFilter">
<property name="authenticationManager" ref="authenticationManager" />
<property name="authenticationSuccessHandler" ref="jwtAuthenticationSuccessHandler" />
</bean>
<sec:authentication-manager alias="authenticationManager">
<sec:authentication-provider ref="jwtAuthenticationProvider" />
</sec:authentication-manager>