我有以下terraform模块,用于在同一计划下设置应用服务:
我正在通过以下配置来调用它:
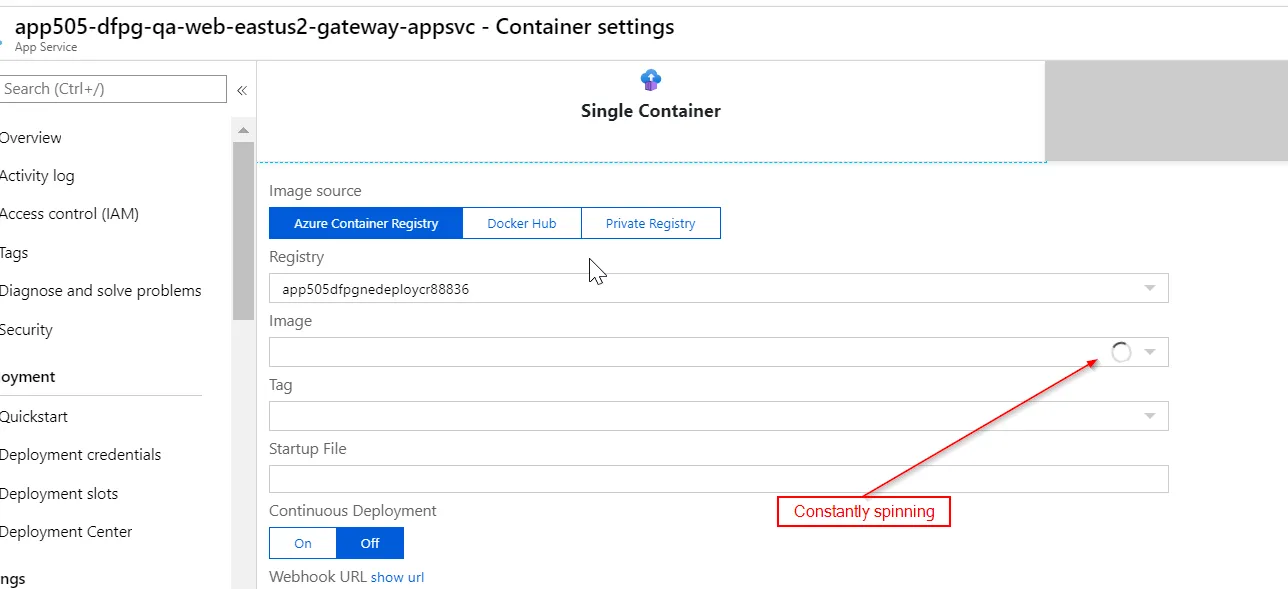
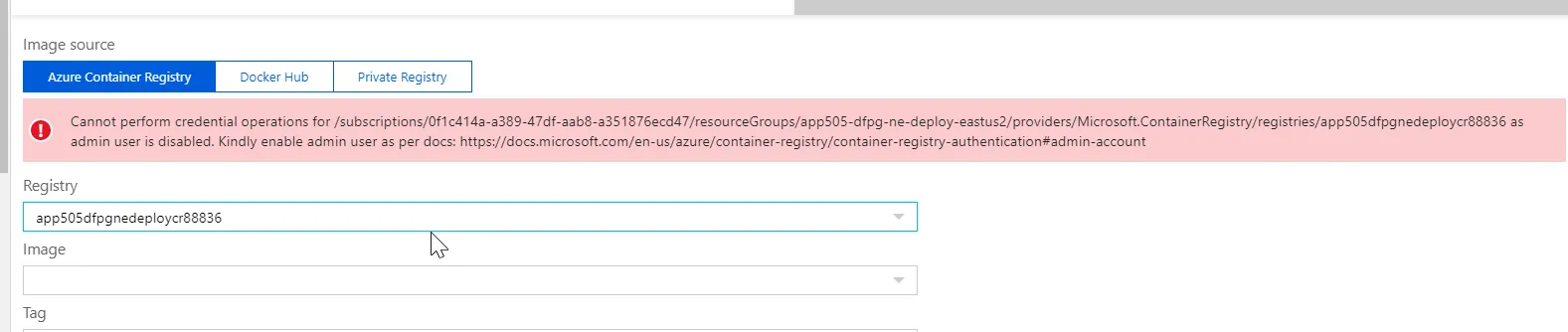
当我应用terraform配置时,一切都被成功创建了,但是在Azure门户中检查创建的应用服务资源时,发现其容器设置没有显示docker镜像: 现在,我可以手动切换到另一个ACR,然后再切回到我想要的ACR,但只能得到这个结果:
这让我感到困惑。根据https://learn.microsoft.com/en-us/azure/container-registry/container-registry-authentication#admin-account,不应使用管理员用户,因此我的ACR没有管理员用户。另一方面,我了解到需要以某种方式配置应用服务与ACR进行身份验证。
那么正确的方法是什么呢?
provider "azurerm" {
}
variable "env" {
type = string
description = "The SDLC environment (qa, dev, prod, etc...)"
}
variable "appsvc_names" {
type = list(string)
description = "The names of the app services to create under the same app service plan"
}
locals {
location = "eastus2"
resource_group_name = "app505-dfpg-${var.env}-web-${local.location}"
acr_name = "app505dfpgnedeploycr88836"
}
resource "azurerm_app_service_plan" "asp" {
name = "${local.resource_group_name}-asp"
location = local.location
resource_group_name = local.resource_group_name
kind = "Linux"
reserved = true
sku {
tier = "Basic"
size = "B1"
}
}
resource "azurerm_app_service" "appsvc" {
for_each = toset(var.appsvc_names)
name = "${local.resource_group_name}-${each.value}-appsvc"
location = local.location
resource_group_name = local.resource_group_name
app_service_plan_id = azurerm_app_service_plan.asp.id
site_config {
linux_fx_version = "DOCKER|${local.acr_name}/${each.value}:latest"
}
app_settings = {
DOCKER_REGISTRY_SERVER_URL = "https://${local.acr_name}.azurecr.io"
}
}
output "hostnames" {
value = {
for appsvc in azurerm_app_service.appsvc: appsvc.name => appsvc.default_site_hostname
}
}
我正在通过以下配置来调用它:
terraform {
backend "azurerm" {
}
}
locals {
appsvc_names = ["gateway"]
}
module "web" {
source = "../../modules/web"
env = "qa"
appsvc_names = local.appsvc_names
}
output "hostnames" {
description = "The hostnames of the created app services"
value = module.web.hostnames
}
容器注册表中有我需要的镜像:
C:\> az acr login --name app505dfpgnedeploycr88836
Login Succeeded
C:\> az acr repository list --name app505dfpgnedeploycr88836
[
"gateway"
]
C:\> az acr repository show-tags --name app505dfpgnedeploycr88836 --repository gateway
[
"latest"
]
C:\>
当我应用terraform配置时,一切都被成功创建了,但是在Azure门户中检查创建的应用服务资源时,发现其容器设置没有显示docker镜像: 现在,我可以手动切换到另一个ACR,然后再切回到我想要的ACR,但只能得到这个结果:
Cannot perform credential operations for /subscriptions/0f1c414a-a389-47df-aab8-a351876ecd47/resourceGroups/app505-dfpg-ne-deploy-eastus2/providers/Microsoft.ContainerRegistry/registries/app505dfpgnedeploycr88836 as admin user is disabled. Kindly enable admin user as per docs: https://learn.microsoft.com/en-us/azure/container-registry/container-registry-authentication#admin-account
这让我感到困惑。根据https://learn.microsoft.com/en-us/azure/container-registry/container-registry-authentication#admin-account,不应使用管理员用户,因此我的ACR没有管理员用户。另一方面,我了解到需要以某种方式配置应用服务与ACR进行身份验证。
那么正确的方法是什么呢?