我尝试在CloudFormation中创建一个模板,其中一个Lambda函数由一个CloudWatch事件规则(每10分钟)触发。在CloudWatch图表中,我可以看到调用但也有所有失败的调用。我认为这是规则角色的问题,但我无法弄清楚它。
以下是我在CloudFormation设计器中可以看到的模板: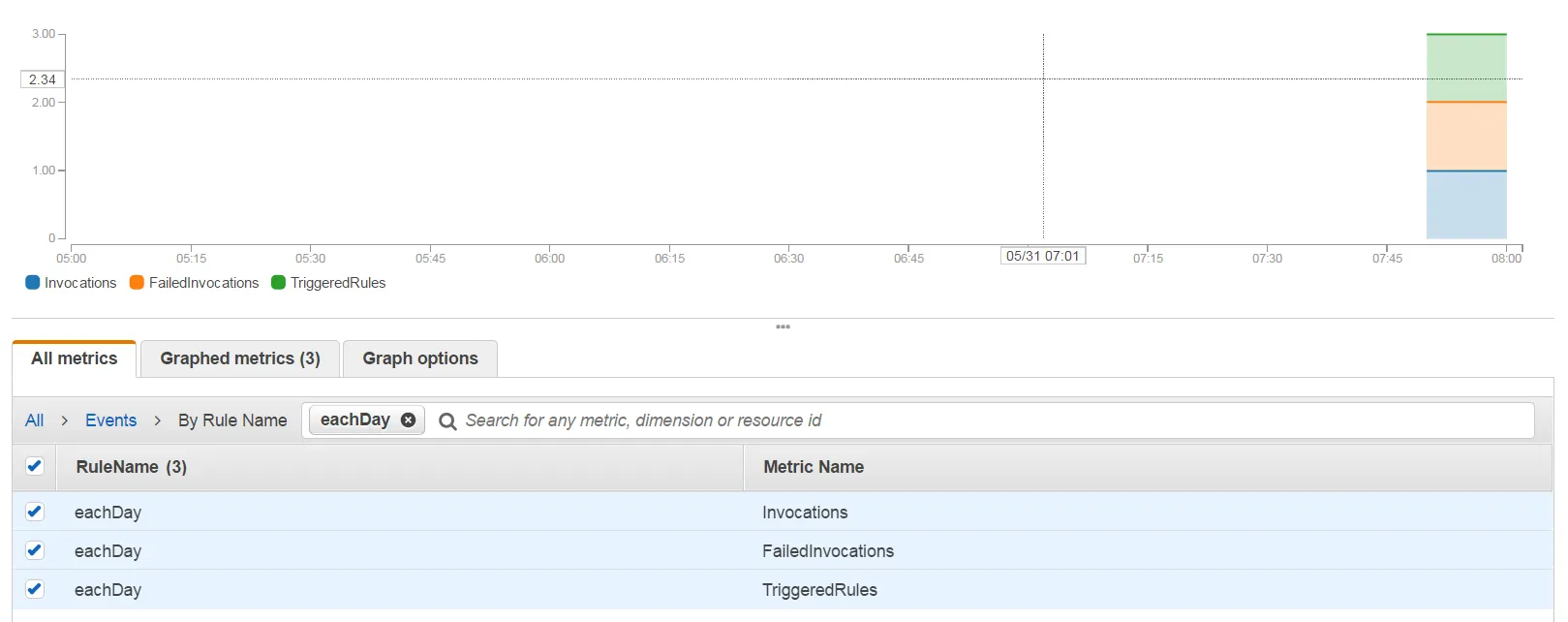
以下是我在CloudFormation设计器中可以看到的模板:

{
"AWSTemplateFormatVersion": "2010-09-09",
"Metadata": {
"AWS::CloudFormation::Designer": {
"d1498a15-7d12-4ec9-bba6-3ba163574a10": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": 450,
"y": 90
},
"z": 1,
"embeds": []
},
"afe4f2cd-0634-4114-8327-1ecf60933475": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": 310,
"y": 90
},
"z": 1,
"embeds": [],
"isrelatedto": [
"d1498a15-7d12-4ec9-bba6-3ba163574a10"
]
},
"c7843bb1-3134-44e7-9463-f9054118e52b": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": 150,
"y": 90
},
"z": 1,
"embeds": [],
"isrelatedto": [
"afe4f2cd-0634-4114-8327-1ecf60933475",
"40b5efaf-5cdd-449e-9155-177461dd4d8e"
]
},
"ef4c0b58-6bb9-46c2-a4b4-64260aa2b35d": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": 310,
"y": -30
},
"z": 1,
"embeds": []
},
"40b5efaf-5cdd-449e-9155-177461dd4d8e": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": 310,
"y": -40
},
"z": 0,
"embeds": [],
"isrelatedto": [
"afe4f2cd-0634-4114-8327-1ecf60933475"
]
}
}
},
"Resources": {
"IAMR3JNYX": {
"Type": "AWS::IAM::Role",
"Properties": {
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "lambda.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
},
"ManagedPolicyArns": [
"arn:aws:iam::aws:policy/CloudWatchLogsFullAccess"
],
"Policies": [
{
"PolicyName": "s3BackupBucket",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:*"
],
"Resource": {
"Fn::Join": [
"",
[
"*"
]
]
}
},
{
"Effect": "Allow",
"Action": [
"s3:*"
],
"Resource": {
"Fn::Join": [
"",
[
"*"
]
]
}
},
{
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents"
],
"Effect": "Allow",
"Resource": "arn:aws:logs:*:*:*"
}
]
}
}
]
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "d1498a15-7d12-4ec9-bba6-3ba163574a10"
}
}
},
"ER1SCU1": {
"Type": "AWS::Events::Rule",
"Properties": {
"Description": "launch the lambda function every 10min",
"Name": "eachDay",
"ScheduleExpression": "cron(0/10 * ? * * *)",
"State": "ENABLED",
"RoleArn": {
"Fn::GetAtt": [
"IAMR25JO4",
"Arn"
]
},
"Targets": [
{
"Arn": {
"Fn::GetAtt": [
"CreateBackUp",
"Arn"
]
},
"Id": "CreateBackUp"
}
]
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "c7843bb1-3134-44e7-9463-f9054118e52b"
}
}
},
"CreateBackUp": {
"Type": "AWS::Lambda::Function",
"Properties": {
"Handler": "index.handler",
"Runtime": "nodejs4.3",
"Timeout": "76",
"Role": {
"Fn::GetAtt": [
"IAMR3JNYX",
"Arn"
]
},
"Code": {
"ZipFile": {
"Fn::Join": [
"",
[
"my function ..."
]
]
}
}
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "afe4f2cd-0634-4114-8327-1ecf60933475"
}
}
},
"IAMR25JO4": {
"Type": "AWS::IAM::Role",
"Properties": {
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "events.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
},
"ManagedPolicyArns": [
"arn:aws:iam::aws:policy/CloudWatchLogsFullAccess"
],
"Policies": [
{
"PolicyName": "InvokeBackUpLambda",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"lambda:*"
],
"Resource": {
"Fn::GetAtt": [
"CreateBackUp",
"Arn"
]
}
},
{
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents"
],
"Effect": "Allow",
"Resource": "arn:aws:logs:*:*:*"
}
]
}
}
]
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "40b5efaf-5cdd-449e-9155-177461dd4d8e"
}
}
}
}
}