我正在按照SQL Server 2008中的数据访问跟踪所述捕获ADO.Net诊断ETW。设置已经生效,生成了一个ETL文件,如果我使用tracerpt,就可以看到ADO.Net跟踪结果:
System.Data, TextA, 0, 0, 0, 0, 17, 0, 0x0000000000000000, 0x000007D0, 0x00003A64, 1, , , {00000000-0000-0000-0000-000000000000}, , 131485096603462277, 450, 2400, 2, "enter_01 <prov.DbConnectionHelper.CreateDbCommand|API> 1# "
System.Data, TextA, 0, 0, 0, 0, 17, 0, 0x0000000000000000, 0x000007D0, 0x00003A64, 1, , , {00000000-0000-0000-0000-000000000000}, , 131485096603469806, 450, 2400, 2, "<sc.SqlCommand.set_Connection|API> 1#, 1# "
System.Data, TextA, 0, 0, 0, 0, 17, 0, 0x0000000000000000, 0x000007D0, 0x00003A64, 1, , , {00000000-0000-0000-0000-000000000000}, , 131485096603469816, 450, 2400, 2, "leave_01 "
System.Data, TextA, 0, 0, 0, 0, 17, 0, 0x0000000000000000, 0x000007D0, 0x00003A64, 1, , , {00000000-0000-0000-0000-000000000000}, , 131485096603471294, 450, 2400, 2, "<sc.SqlCommand.set_CommandText|API> 1#, '"
System.Data, TextA, 0, 0, 0, 0, 17, 0, 0x0000000000000000, 0x000007D0, 0x00003A64, 1, , , {00000000-0000-0000-0000-000000000000}, , 131485096603474160, 450, 2400, 2, "select cast(serverproperty('EngineEdition') as int)"
System.Data, TextA, 0, 0, 0, 0, 17, 0, 0x0000000000000000, 0x000007D0, 0x00003A64, 1, , , {00000000-0000-0000-0000-000000000000}, , 131485096603474174, 450, 2400, 2, "' "
System.Data, TextA, 0, 0, 0, 0, 17, 0, 0x0000000000000000, 0x000007D0, 0x00003A64, 1, , , {00000000-0000-0000-0000-000000000000}, , 131485096603523068, 450, 2400, 2, "<sc.SqlCommand.ExecuteReader|INFO> 1#, Command executed as SQLBATCH. "
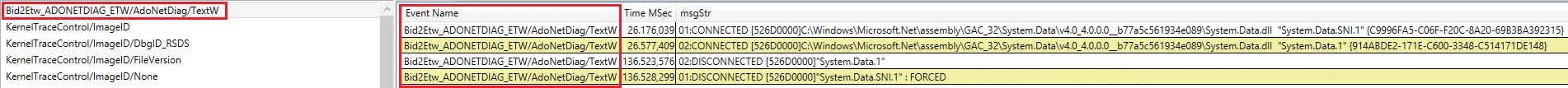
但是,如果我将相同的ETL加载到WPA中,我看不到有关捕获事件的任何有用信息。该提供程序的所有事件都显示事件名称<Unknown>,事件类型经典,并且没有有关实际ADO.Net事件信息的信息(即跟踪器pt CSV输出中的最右侧列):
Line #, Provider Name, Task Name, Type (Opcode/Type ), Opcode Name, Id, Process, Annotation, Event Name, Event Type, Message, Cpu, ThreadId, Message, UserDataLength, Time (s)
1, 914abde3-171e-c600-3348-c514171de148, <Unknown>, 17, , 0, Unknown, <Not Annotated>, <Unknown>, Classic, , 3, 14056, , 0, 22.877068496
2, 914abde3-171e-c600-3348-c514171de148, <Unknown>, 17, , 0, Unknown, <Not Annotated>, <Unknown>, Classic, , 0, 14056, , 0, 22.877265256
3, 914abde3-171e-c600-3348-c514171de148, <Unknown>, 17, , 0, Unknown, <Not Annotated>, <Unknown>, Classic, , 0, 14056, , 0, 22.877275482
4, 914abde3-171e-c600-3348-c514171de148, <Unknown>, 17, , 0, Unknown, <Not Annotated>, <Unknown>, Classic, , 0, 14056, , 0, 22.877276892
5, 914abde3-171e-c600-3348-c514171de148, <Unknown>, 17, , 0, Unknown, <Not Annotated>, <Unknown>, Classic, , 0, 14056, , 0, 22.877299460
6, 914abde3-171e-c600-3348-c514171de148, <Unknown>, 17, , 0, Unknown, <Not Annotated>, <Unknown>, Classic, , 0, 14056, , 0, 22.877301223
7, 914abde3-171e-c600-3348-c514171de148, <Unknown>, 17, , 0, Unknown, <Not Annotated>, <Unknown>, Classic, , 1, 13276, , 0, 23.061972110
8, 914abde3-171e-c600-3348-c514171de148, <Unknown>, 17, , 0, Unknown, <Not Annotated>, <Unknown>, Classic, , 1, 13276, , 0, 23.061975636
9, 914abde3-171e-c600-3348-c514171de148, <Unknown>, 17, , 0, Unknown, <Not Annotated>, <Unknown>, Classic, , 1, 13276, , 0, 23.062004550
10, 914abde3-171e-c600-3348-c514171de148, <Unknown>, 17, , 0, Unknown, <Not Annotated>, <Unknown>, Classic, , 1, 13276, , 0, 23.063588859
11, 914abde3-171e-c600-3348-c514171de148, <Unknown>, 17, , 0, Unknown, <Not Annotated>, <Unknown>, Classic, , 1, 13276, , 0, 23.063617421
既然我捕获的所有其他数据都可以在WPA中分析,我想知道ADO.Net诊断提供程序有什么不同之处,以至于事件对WPA来说如此不透明?