我已经安装了VirtualBox并在VirtualBox虚拟机中安装了Ubuntu服务器版本。我的宿主机是Windows 10。
我还在我的Windows宿主机上安装了Docker。 我的意图是在Windows上使用docker CLI连接到VM内部的docker daemon(服务器)。
我已经在Ubuntu VM中进行了更改,并使其监听端口2375。
tcp 0 0 127.0.0.1:2375 0.0.0.0:* LISTEN 2305/dockerd
我在我的Windows主机上设置了环境变量DOCKER_HOST为虚拟机的IP地址和端口。
set DOCKER_HOST=tcp://192.168.56.107:2375
我的Windows机器IP地址是192.168.56.1,ping测试正常。
Pinging 192.168.56.107 with 32 bytes of data:
Reply from 192.168.56.107: bytes=32 time<1ms TTL=64
Reply from 192.168.56.107: bytes=32 time<1ms TTL=64
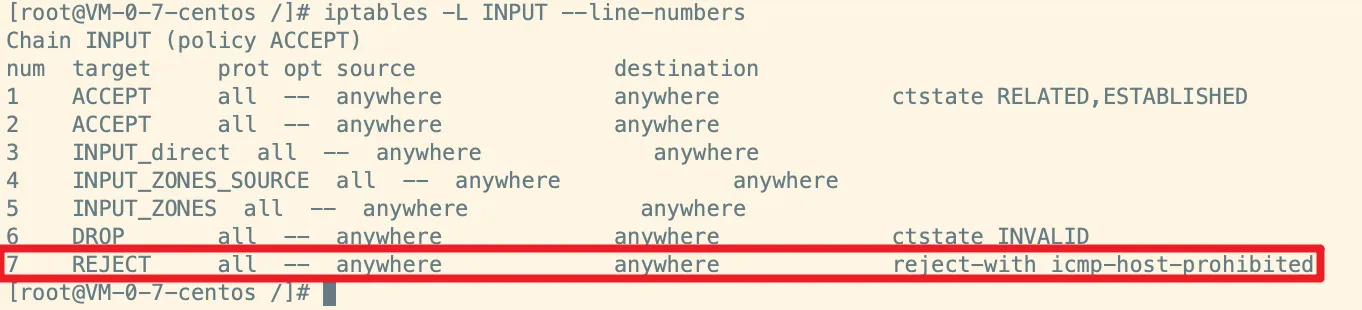
但是当我尝试从我的Windows电脑连接时,会出现以下错误:
error during connect: Get http://192.168.56.107:2375/v1.27/info: dial tcp 192.168.56.107:2375: connectex: No connection could be made because the target machine actively refused it.
请查看Docker信息输出:
controller@ubuntuserver:~$ docker info
Containers: 4
Running: 0
Paused: 0
Stopped: 4
Images: 2
Server Version: 18.09.6
Storage Driver: overlay2
Backing Filesystem: extfs
Supports d_type: true
Native Overlay Diff: true
Logging Driver: json-file
Cgroup Driver: cgroupfs
Plugins:
Volume: local
Network: bridge host macvlan null overlay
Log: awslogs fluentd gcplogs gelf journald json-file local logentries splunk syslog
Swarm: inactive
Runtimes: runc
Default Runtime: runc
Init Binary: docker-init
containerd version: bb71b10fd8f58240ca47fbb579b9d1028eea7c84
runc version: 2b18fe1d885ee5083ef9f0838fee39b62d653e30
init version: fec3683
Security Options:
apparmor
seccomp
Profile: default
Kernel Version: 4.15.0-50-generic
Operating System: Ubuntu 18.04.2 LTS
OSType: linux
Architecture: x86_64
CPUs: 2
Total Memory: 7.79GiB
Name: ubuntuserver
ID: AWDW:34ET:4J2J:2NWB:UPK7:EQHB:W64E:22AT:W6J4:BMRD:NDO6:CNR2
Docker Root Dir: /var/lib/docker
Debug Mode (client): false
Debug Mode (server): false
Registry: https://index.docker.io/v1/
Labels:
Experimental: false
Insecure Registries:
127.0.0.0/8
Live Restore Enabled: false
Product License: Community Engine
WARNING: API is accessible on http://127.0.0.1:2375 without encryption.
Access to the remote API is equivalent to root access on the host. Refer
to the 'Docker daemon attack surface' section in the documentation for
more information: https://docs.docker.com/engine/security/security/#docker-daemon-attack-surface
WARNING: No swap limit support
cat /lib/systemd/system/docker.service
[Unit]
Description=Docker Application Container Engine
Documentation=https://docs.docker.com
BindsTo=containerd.service
After=network-online.target firewalld.service containerd.service
Wants=network-online.target
Requires=docker.socket
[Service]
Type=notify
# the default is not to use systemd for cgroups because the delegate issues still
# exists and systemd currently does not support the cgroup feature set required
# for containers run by docker
ExecStart=/usr/bin/dockerd -H fd:// -H tcp://0.0.0.0:2375 --containerd=/run/containerd/containerd.sock
ExecReload=/bin/kill -s HUP $MAINPID
TimeoutSec=0
RestartSec=2
Restart=always
# Note that StartLimit* options were moved from "Service" to "Unit" in systemd 229.
# Both the old, and new location are accepted by systemd 229 and up, so using the old location
# to make them work for either version of systemd.
StartLimitBurst=3
# Note that StartLimitInterval was renamed to StartLimitIntervalSec in systemd 230.
# Both the old, and new name are accepted by systemd 230 and up, so using the old name to make
# this option work for either version of systemd.
StartLimitInterval=60s
# Having non-zero Limit*s causes performance problems due to accounting overhead
# in the kernel. We recommend using cgroups to do container-local accounting.
LimitNOFILE=infinity
LimitNPROC=infinity
LimitCORE=infinity
# Comment TasksMax if your systemd version does not supports it.
# Only systemd 226 and above support this option.
TasksMax=infinity
# set delegate yes so that systemd does not reset the cgroups of docker containers
Delegate=yes
# kill only the docker process, not all processes in the cgroup
KillMode=process
[Install]
WantedBy=multi-user.target
你能帮我解决这个问题吗?
controller@ubuntuserver:~$ docker -H 192.168.56.107:2375 ps Cannot connect to the Docker daemon at tcp://192.168.56.107:2375. Is the docker daemon running? controller@ubuntuserver:~$ docker -H localhost:2375 ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES- SRajenp0s8: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.56.107 netmask 255.255.255.0 broadcast 192.168.56.255 inet6 fe80::a00:27ff:fe70:dff2 prefixlen 64 scopeid 0x20<link>- SRajExecStart=/usr/bin/dockerd -H fd:// -H tcp://0.0.0.0:2375 ...您需要将0.0.0.0:2375替换为您的 IP 地址。 - Marc ABOUCHACRA