我正在尝试生成一个由存储在Azure KeyVault中的KeyPair自签名的证书。
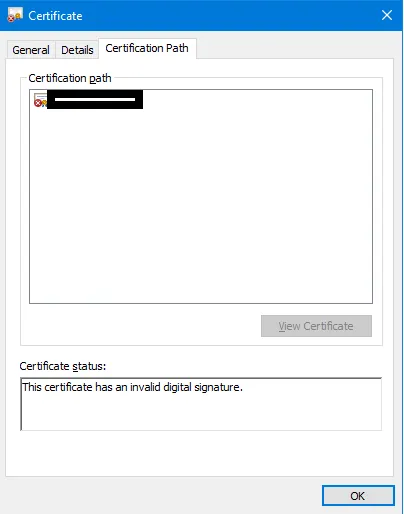
我的最终结果是一个带有无效签名的证书:
生成证书参数:
DateTime startDate = DateTime.Now.AddDays(-30);
DateTime expiryDate = startDate.AddYears(100);
BigInteger serialNumber = new BigInteger(32, new Random());
X509V1CertificateGenerator certGen = new X509V1CertificateGenerator();
X509Name selfSignedCA = new X509Name("CN=Test Root CA");
certGen.SetSerialNumber(serialNumber);
certGen.SetIssuerDN(selfSignedCA); //Self Signed
certGen.SetNotBefore(startDate);
certGen.SetNotAfter(expiryDate);
certGen.SetSubjectDN(selfSignedCA);
获取指向 Azure KeyVault 存储密钥(类似 HSM 服务)的引用:
//Create a client connector to Azure KeyVault
var keyClient = new Azure.Security.KeyVault.Keys.KeyClient(
vaultUri: new Uri("https://xxxx.vault.azure.net/"),
credential: new ClientSecretCredential(
tenantId: "xxxx", //Active Directory
clientId: "xxxx", //Application id?
clientSecret: "xxxx"
)
);
var x = keyClient.GetKey("key-new-ec"); //Fetch the reference to the key
成功检索到密钥。 接下来,我尝试使用密钥的公共数据生成ECPublicKeyParameters对象:
X9ECParameters x9 = ECNamedCurveTable.GetByName("P-256");
Org.BouncyCastle.Math.EC.ECCurve curve = x9.Curve;
var ecPoint = curve.CreatePoint(new Org.BouncyCastle.Math.BigInteger(1, x.Value.Key.X), new Org.BouncyCastle.Math.BigInteger(1, x.Value.Key.Y));
ECDomainParameters dParams = new ECDomainParameters(curve, ecPoint, x9.N);
ECPublicKeyParameters pubKey = new ECPublicKeyParameters(ecPoint, dParams);
certGen.SetPublicKey(pubKey); //Setting the certificate's public key with the fetched one
下一步是生成由该密钥签名的证书。我实现了一个新的ISignatureFactory对象,应该使用KeyVault的外部签名函数进行签名:
AzureKeyVaultSignatureFactory customSignatureFactory = new AzureKeyVaultSignatureFactory(1);
Org.BouncyCastle.X509.X509Certificate cert = certGen.Generate(customSignatureFactory);
这是我的自定义AzureKeyVaultSignatureFactory:
public class AzureKeyVaultSignatureFactory : ISignatureFactory
{
private readonly int _keyHandle;
public AzureKeyVaultSignatureFactory(int keyHandle)
{
this._keyHandle = keyHandle;
}
public IStreamCalculator CreateCalculator()
{
var sig = new CustomAzureKeyVaultDigestSigner(this._keyHandle);
sig.Init(true, null);
return new DefaultSignatureCalculator(sig);
}
internal class CustomAzureKeyVaultDigestSigner : ISigner
{
private readonly int _keyHandle;
private byte[] _input;
public CustomAzureKeyVaultDigestSigner(int keyHandle)
{
this._keyHandle = keyHandle;
}
public void Init(bool forSigning, ICipherParameters parameters)
{
this.Reset();
}
public void Update(byte input)
{
return;
}
public void BlockUpdate(byte[] input, int inOff, int length)
{
this._input = input.Skip(inOff).Take(length).ToArray();
}
public byte[] GenerateSignature()
{
//Crypto Client (Specific Key)
try
{
//Crypto Client (Specific Key)
CryptographyClient identitiesCAKey_cryptoClient = new CryptographyClient(
keyId: new Uri("https://xxxx.vault.azure.net/keys/key-new-ec/xxxx"),
credential: new ClientSecretCredential(
tenantId: "xxxx", //Active Directory
clientId: "xxxx", //Application id?
clientSecret: "xxxx"
)
);
SignResult signResult = identitiesCAKey_cryptoClient.SignData(SignatureAlgorithm.ES256, this._input);
return signResult.Signature;
}
catch (Exception ex)
{
throw ex;
}
return null;
}
public bool VerifySignature(byte[] signature)
{
return false;
}
public void Reset() { }
public string AlgorithmName => "SHA-256withECDSA";
}
public object AlgorithmDetails => new AlgorithmIdentifier(X9ObjectIdentifiers.ECDsaWithSha256, DerNull.Instance);
}
然后我将证书转换并写入文件:
//convert to windows type 2 and get Base64
X509Certificate2 cert2 = new X509Certificate2(DotNetUtilities.ToX509Certificate(cert));
byte[] encoded = cert2.GetRawCertData();
string certOutString = Convert.ToBase64String(encoded);
System.IO.File.WriteAllBytes(@"test-signed2.cer", encoded); //-this is good!
我做错了什么?也许只用X/Y构建ECCurve还不够吗?
谢谢!
public string AlgorithmName => "SHA-256withRSA";。 - President James K. Polk