我正在尝试编写代码来从DLL或EXE中读取签名(证书)。大多数DLL或EXE只有一个签名,我的代码可以正确地读取与此签名相关的所有证书。更具体地说,它读取签名证书、其颁发者(非根证书)、计数器签名证书(带有时间戳)以及其颁发者(非根证书)。我有两个样本程序,一个是C++,一个是C#,它们都返回相同的证书。这是C#代码,C++代码要长100倍:)
static void Main(string[] args)
{
X509Certificate2Collection collection = new X509Certificate2Collection();
collection.Import(args[0]);
}
但是有一些DLL具有两个签名,如文件属性/数字签名中所示,例如C:\ Program Files(x86)\ Microsoft SQL Server \ 80 \ Tools \ Binn \ msvcr71.dll:
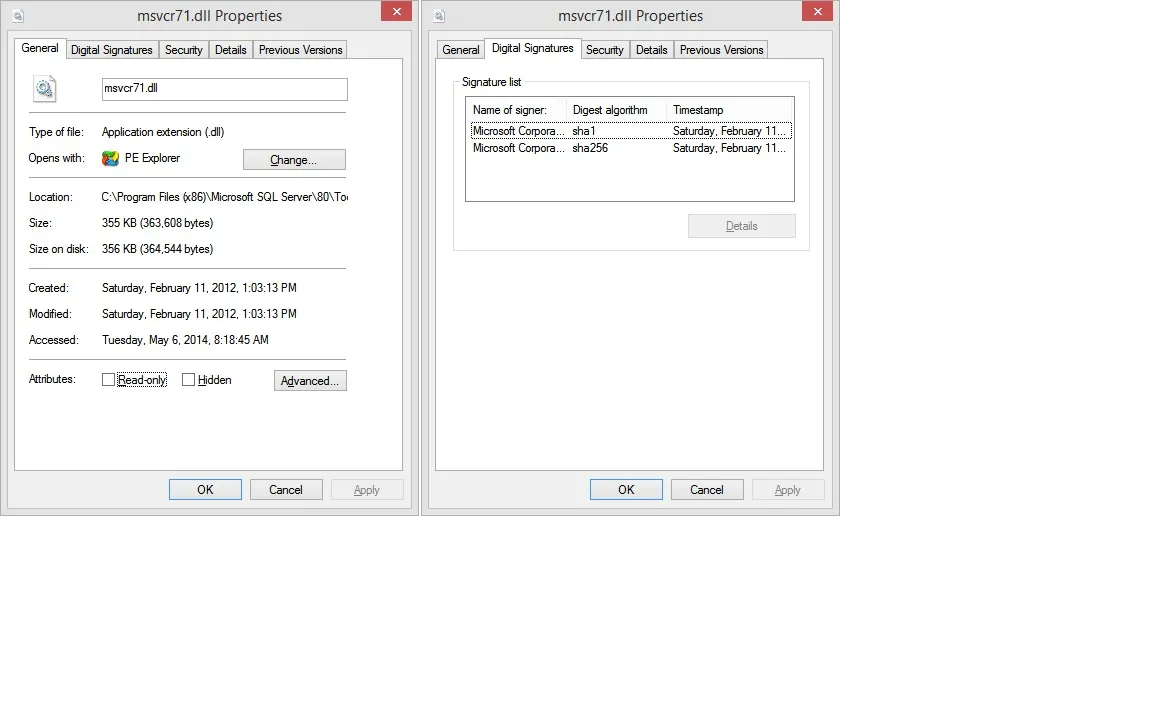
对于这个DLL,我的代码只读取与第一个签名相关联的证书。
我还尝试使用signtool,它返回与我的代码相同的信息:第一个证书(及其路径)和计数签名(及其路径)。但也请注意末尾的错误。
C:\Windows>signtool verify /d /v "C:\Program Files (x86)\Microsoft SQL Server\80\Tools\Binn\msvcr71.dll"
Verifying: C:\Program Files (x86)\Microsoft SQL Server\80\Tools\Binn\msvcr71.dll
Signature Index: 0 (Primary Signature)
Hash of file (sha1): 33BBCCF6326276B413A1ECED1BF7842A6D1DDA07
Signing Certificate Chain:
Issued to: Microsoft Root Certificate Authority
Issued by: Microsoft Root Certificate Authority
Expires: Sun May 09 19:28:13 2021
SHA1 hash: CDD4EEAE6000AC7F40C3802C171E30148030C072
Issued to: Microsoft Code Signing PCA
Issued by: Microsoft Root Certificate Authority
Expires: Wed Jan 25 19:32:32 2017
SHA1 hash: FDD1314ED3268A95E198603BA8316FA63CBCD82D
Issued to: Microsoft Corporation
Issued by: Microsoft Code Signing PCA
Expires: Fri Feb 01 18:49:17 2013
SHA1 hash: 8849D1C0F147A3C8327B4038783AEC3E06C76F5B
The signature is timestamped: Sat Feb 11 14:03:12 2012
Timestamp Verified by:
Issued to: Microsoft Root Certificate Authority
Issued by: Microsoft Root Certificate Authority
Expires: Sun May 09 19:28:13 2021
SHA1 hash: CDD4EEAE6000AC7F40C3802C171E30148030C072
Issued to: Microsoft Time-Stamp PCA
Issued by: Microsoft Root Certificate Authority
Expires: Sat Apr 03 09:03:09 2021
SHA1 hash: 375FCB825C3DC3752A02E34EB70993B4997191EF
Issued to: Microsoft Time-Stamp Service
Issued by: Microsoft Time-Stamp PCA
Expires: Thu Oct 25 16:42:17 2012
SHA1 hash: FC33104FAE31FB538749D5F2D17FA0ECB819EAE5
SignTool Error: The signing certificate is not valid for the requested usage.
This error sometimes means that you are using the wrong verification
policy. Consider using the /pa option.
Number of files successfully Verified: 0
Number of warnings: 0
Number of errors: 1
我有两个问题: - 第二个签名的目的是什么 - 如何阅读它(到目前为止只有Windows资源管理器文件属性对话框可以显示它)。
谢谢!
SHA-1签名,因为 SHA-1 的冲突抵抗能力不足。它们仍然留在今天是为了向后兼容性。 - ahmd0